RESEARCH
Our Information Security Research Contributions
- 2019
VB2019 - The security products we deserve
- 2019
USENIX 2019 - Embracing the "hack"
- 2017
BlackHat 2017 - Fighting the Previous War
- 2017
T2.fi - Learning the wrong lessons from Offense
- 2015
BlackHat Europe 2015 - Keynote
- 2015
BlackHat 2015 - Bring back the Honeypots
- 2015
Troopers15 - The hard thing about the Hard Things
- 2014
Hack in the Box - Weapons of Mass Distraction - Sock Puppetry for Fun & Profit
- 2014
Navixia - Ignore the Politics: Lessons from the Snowden Affair
- 2014
ITWeb Security - What the Snowden Affair means for South Africa
- 2013
Acumen - Your company's security posture is probably horrible (but it might be OK)
- 2013
44Con - A talk about (InfoSec) talks
- 2013
BlackHat - 2013 - The Year in Review
- 2012
SecData - What should be keeping you up at night
- 2012
ITWeb Security Summit - The things we don't say
- 2011
BruCon / Hack in the Box / Troopers - You & Your Research
- 2011
44Con - Penetration Testing Considered Harmful Today
- 2011
Paper - On-screen Keyboards Considered Harmful
- 2011
ZaCon2/ITWeb - Fig Leaf Security
- 2010
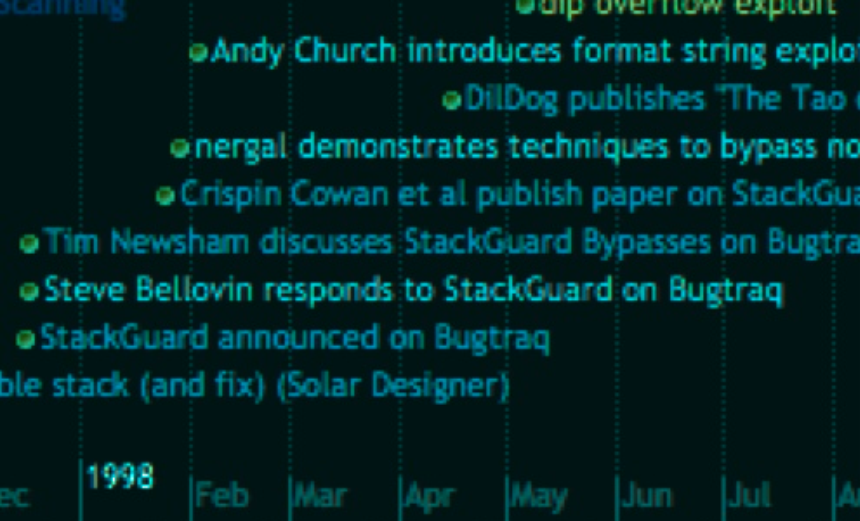
BlackHat USA - Memory Corruption Attacks: The (almost) Complete History
- 2010
CCDCOE - Conference on Cyber Conflict - Why your threat model is probably wrong
- 2009
BlackHat USA - Clobbering the Cloud
- 2009
ISSA - An examination of the Generic Exploit Prevention Mechanisms on Apples Leopard Operating System
- 2009
ITWeb Security Summit - One bad Apple
- 2008
BlackHat USA - Pushing the Camel through the Eye of the Needle
- 2008
ITWeb Security Summit - When the Rubber hits the Road - Mobile Insecurity
- 2007
BlackHat USA - Its all about the Timing
- 2007
ITWeb Security Summit - Drawing Blood from a Stone
- 2007
ITWeb Security Summit - Thats Really not the Point
- 2006
BlackHat USA - A Tale of Two Proxies
- 2006
ITWeb Security Summit - Truth or Scare
- 2006
ISSA - When good code goes bad!
- 2006
IDC IT Security Roadshow - The difference between a Duck
- 2005
RECon - Web Application Hacking
- 2004
BlackHat USA - When the Tables Turn
- 2004
Microsoft Tech-Ed - Common Attack Vectors and Protection in IIS6
- 2003
ISSA - Hacking Web Applications
- 2002
BlackHat USA - Setiri - Advances in Trojan Technology
SKUNKWORKS SOFTWARE
Some Things We Have to Build, Even if it's Just for Us
BOOKS
We're Proud to have Contributed to these Information Security Publications

STEALING THE NETWORK
How to Own a Continent

SPECIAL OPS
Host & Network Security for Microsoft, UNIX & Oracle

SQL INJECTION
Attacks and Defense

PENETRATIONS TESTER'S
Open Source Toolkit

AGGRESSIVE NETWORK SELF-DEFENSE
I’m Mad as Hell, and I’m Not Gonna Take It Anymore!

NESSUS NETWORK AUDITING
Second Edition